Back to: Computer Science JSS 3
Welcome to class!
In today’s class, we’re going to be talking about the sources and examples of computer viruses. I trust you will enjoy the class!
Sources and Examples of Computer Virus
In today’s digital world, understanding computer viruses is crucial. Just like their biological counterparts, these malicious programs can wreak havoc on your system, stealing data, corrupting files, and causing major headaches. So, buckle up and get ready to learn about the sneaky ways viruses infiltrate our devices and some infamous examples to watch out for.
Where do these digital villains(viruses) come from?
Viruses lurk in various dark corners of the internet, waiting to pounce. Here are some common sources:
Infected Websites: Clicking on malicious ads, links, or downloads on untrusted websites can unleash a virus onto your system. Be cautious and stick to reputable sources!
Email Attachments: Don’t be fooled by curiosity! Never open suspicious attachments, even if they seem to come from someone you know. Their account might be hacked!
Free Downloads: Free software, games, or music from untrusted sources often come bundled with unwanted guests – viruses! Stick to official websites and app stores.
Removable Media: USB drives, CDs, and DVDs can be carriers of viruses. Only use media from trusted sources and scan them before opening any files.
Social Media: Malicious links and fake profiles can spread viruses on social media platforms. Be vigilant and avoid clicking on suspicious content.
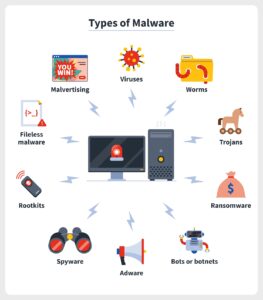
Types of Computer Viruses 
Just like superheroes, viruses come in different shapes and sizes:
Trojan Horses: Disguised as legitimate software, they trick you into installing them, then unleash their harmful payload. Think of them as wolves in sheep’s clothing!
Worms: These self-replicating creatures spread rapidly through networks, infecting multiple devices like wildfire. Imagine a virus with superpowers of speed and reach!
Ransomware: These nasty villains lock your files and demand a ransom to unlock them. Don’t give in! Back up your data regularly and have a good antivirus program.
Spyware: These sneaky characters silently monitor your activity and steal your personal information. Be mindful of what permissions you grant to apps and websites.
Examples of Computer Viruses
Remember the names? Infamous Virus Examples:
I Love You: This 2000 email worm exploited people’s curiosity, tricking them into opening an attachment that spread like wildfire.
WannaCry: This 2017 ransomware attack crippled hospitals and businesses worldwide, highlighting the dangers of cyber threats.
Stuxnet: This sophisticated worm targeted industrial control systems, showcasing the potential of viruses to disrupt critical infrastructure.
How to Stay Protected!
- By understanding the sources and types of viruses, you can be more vigilant online. Here are some tips to stay safe:
- Install a good antivirus program and keep it updated.
- Be cautious with email attachments and downloads.
- Only use trusted websites and app stores.
- Keep your software updated to patch security vulnerabilities.
- Back up your data regularly.
- Be skeptical of anything that seems too good to be true online.
By following these tips and staying informed, you can become a cybersecurity hero and keep your digital devices safe from the clutches of viruses!
We have come to the end of today’s class. I hope you enjoyed the class!
In the next class, we shall be discussing Computer virus warning signs.
In case you require further assistance or have any questions, feel free to ask in the comment section below, and trust us to respond as soon as possible. Cheers!
Question Time:
- What are some recent examples of major virus outbreaks and their impact?
- How can social engineering be used to spread viruses?
- What are the potential consequences of a virus infection for individuals and businesses?
- How can outdated software become a security risk in relation to viruses?
- Differentiate between a virus, worm, and Trojan horse. Provide real-world examples.


